Troubleshooting Firewall Issues Using Wireshark
In a previous post, the basics of Wireshark were covered, which focused on how to analyze network traffic. Another use case of Wireshark that I have found useful is to troubleshoot firewall issues affecting a client and server in a local or remote environment. For example, when attempting to access a docker container located on another subnet, the attempt may not be successful due to the firewall on the server which is blocking inbound traffic to the docker container. Since this is a firewall-related issue, Wireshark can be used to help troubleshoot this, which this post will demonstrate.
Setting up a Test Server
For this demonstration, I will be using python to host an HTTP server running on a virtual machine and I will attempt to access it from another virtual machine acting as the client. Both of these virtual machines are running in a local environment and are located on different subnets - the IP address of the server is 10.1.0.3 and the client's IP address is 192.168.2.128. An HTTP server is started by running the below command:
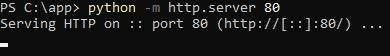
Server Blocked By Firewall
In the first test, the firewall on the server will not have any rules configured that allow inbound HTTP traffic on port 80. As a result, attempting to access the HTTP server from the client will not work:
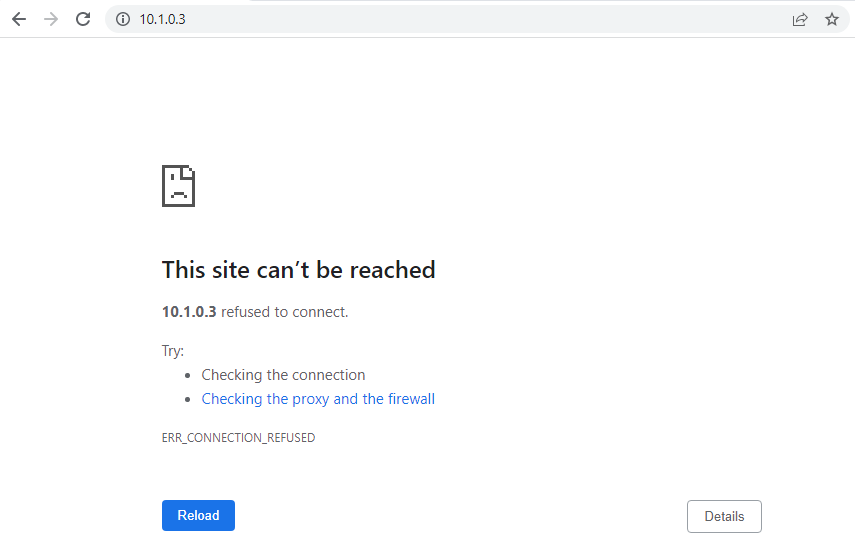
We can verify this by starting a live capture on the client using Wireshark and adding the filter tcp.port == 80 to only show traffic on port 80 and then try accessing http://10.1.0.3. Here we can see a sequence of three SYN packets that were sent from the client to the server:
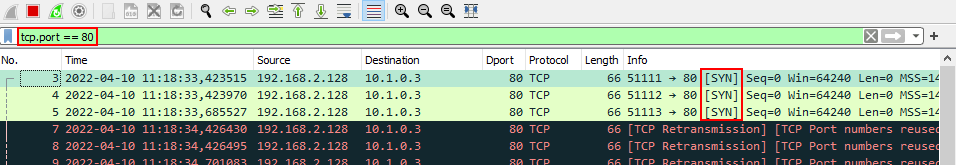
For a connection that is allowed, we would have observed the TCP three-way handshake where the first three packets would have a SYN, SYN-ACK and ACK flags set respectively. Since we are instead seeing a sequence of SYN packets, this suggests that the connection has been blocked by the firewall.
Server Allowed by Firewall
Now that it appears that the connection was blocked, let's add a firewall rule to allow inbound HTTP traffic on the server using powershell (running as admin):
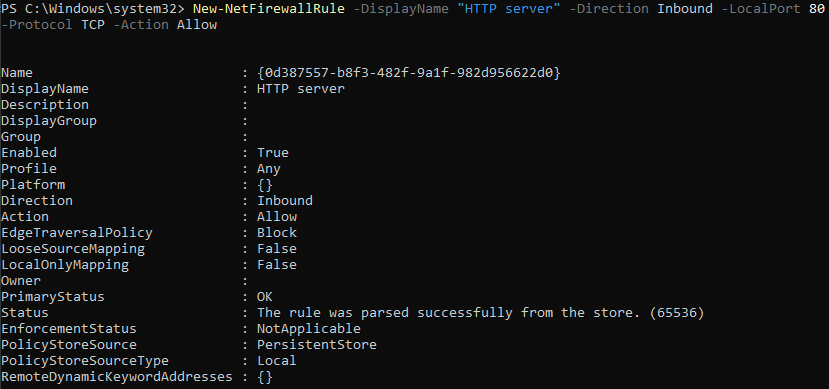
After adding the above rule and navigating to http://10.1.0.3 on the client, the page is successfully loaded:
Looking at the traffic that appeared in Wireshark, we can see that the SYN, SYN-ACK and ACK packets were sent at the beginning of the connection, which confirms that a TCP three-way handshake occurred and that the connection was allowed. We can also see that subsequent packets include a GET request that was sent from the client and that the server responded with an HTTP 200 which indicates that the request was successful:
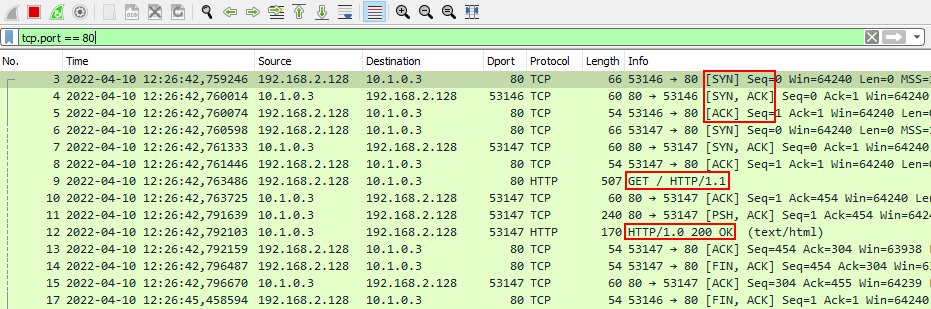
Based on the above troubleshooting, we identified that the client could not initially connect to the server due to the firewall that was blocking the connection. While this demonstration was conducted in a local environment, the same steps can be followed to identify if a firewall is blocking a remote connection.
tags: firewall networking wireshark